See Beyond Your Perimeter
Threat Intelligence & Digital Risk Protection

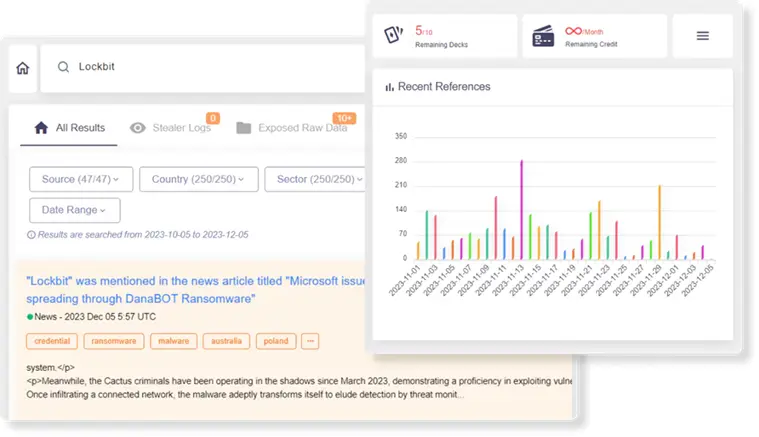
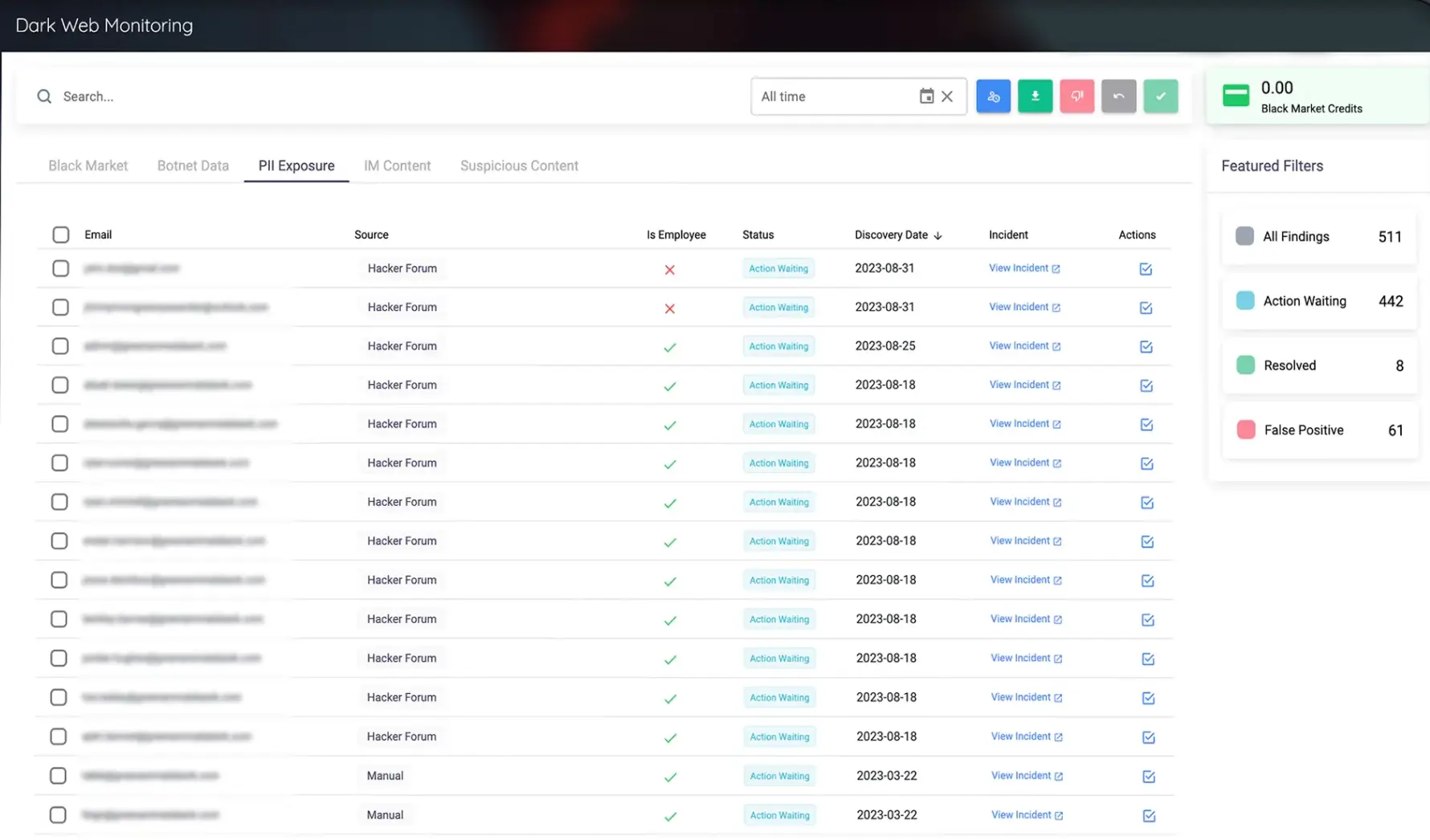
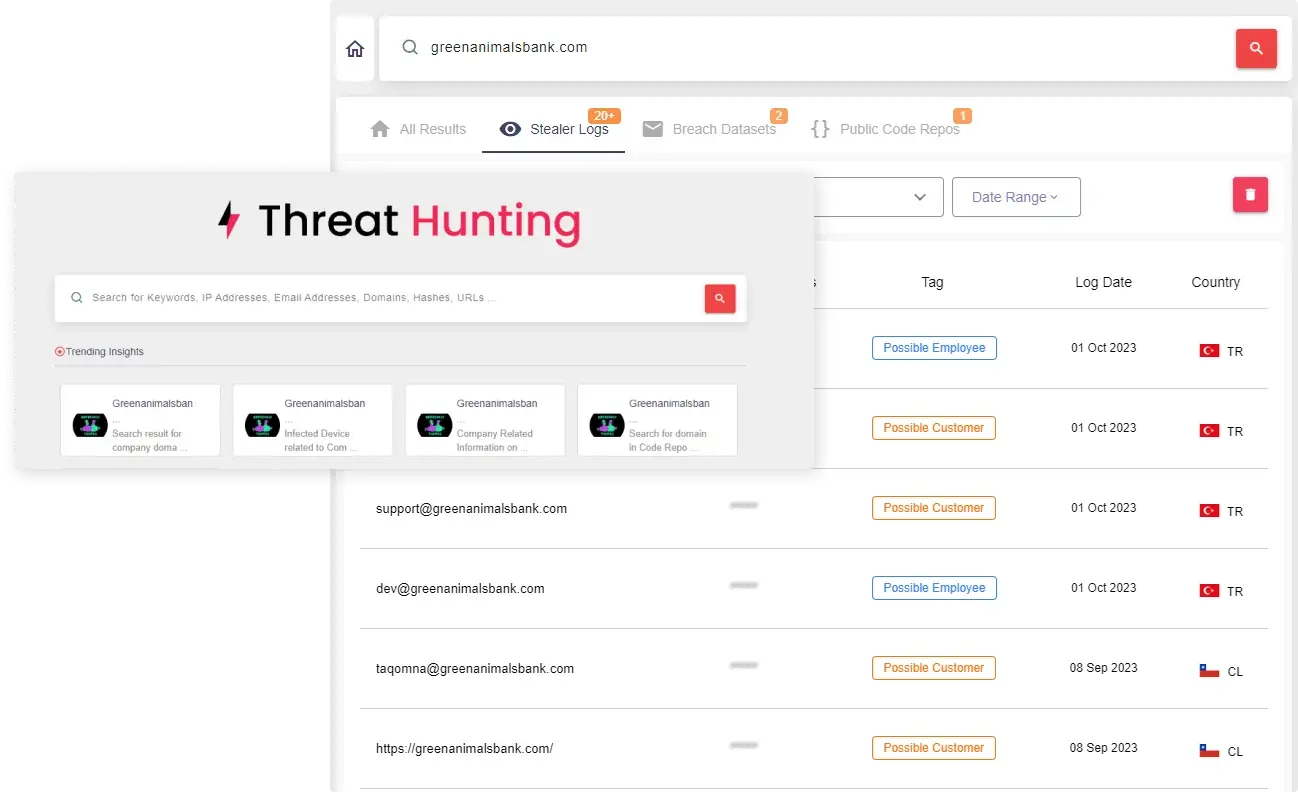
Dark Web Monitoring
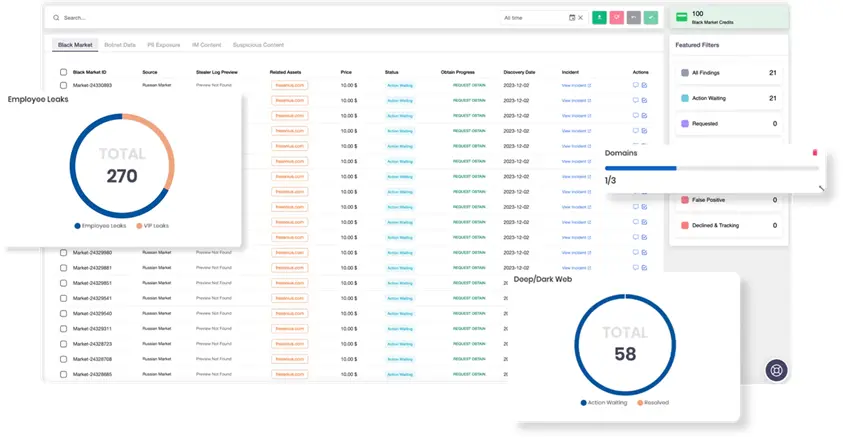
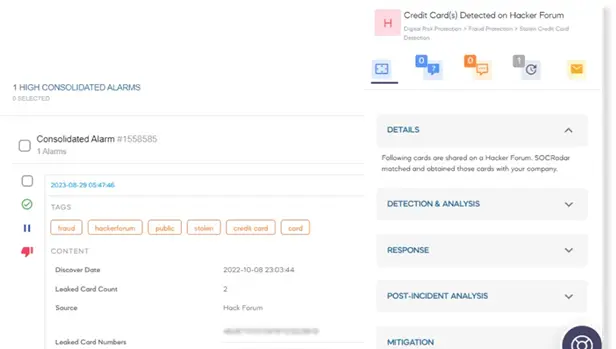
Detect and report compromised credentials, stealer logs, and leaked data across marketplaces, forums, and Telegram channels. Learn More

External Attack Surface Management
Identify, map, and monitor public-facing digital assets — domains, IPs, exposed services — reducing blind spots. Learn More

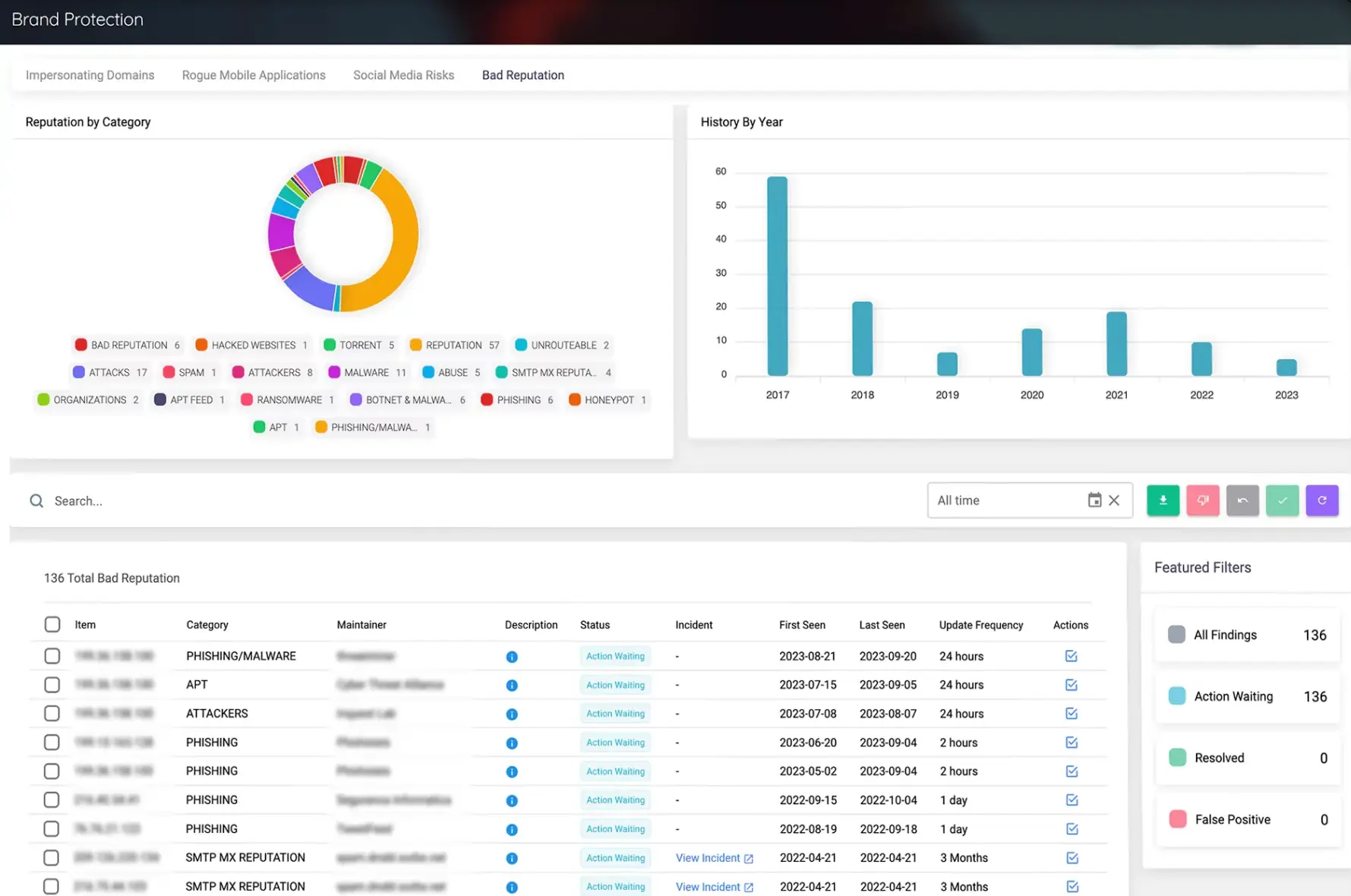
Brand & Identity Protection
Detect and take down typosquatting domains, social impersonation, malicious brand mentions, and executive targeting campaigns. Learn More

Cyber Threat Intelligence
Continuously ingest and correlate multi-source intelligence feeds — combining commercial, open-source, and proprietary recon data.
Your One-Stop Dark Web Solution
Think Like a Hacker, Defend Like a Pro
Guard Your Brand, Strengthen Your Trust
Your Dynamic Shield Against Cyber Adversaries
Your Early Warning System Against Hackers.
Competitive pricing
Starting at:
$ 5,999.00 / year
Dark Web Monitoring
Start NowDark Web Monitoring
- Covers 1 domain
- Blackmarket Monitoring
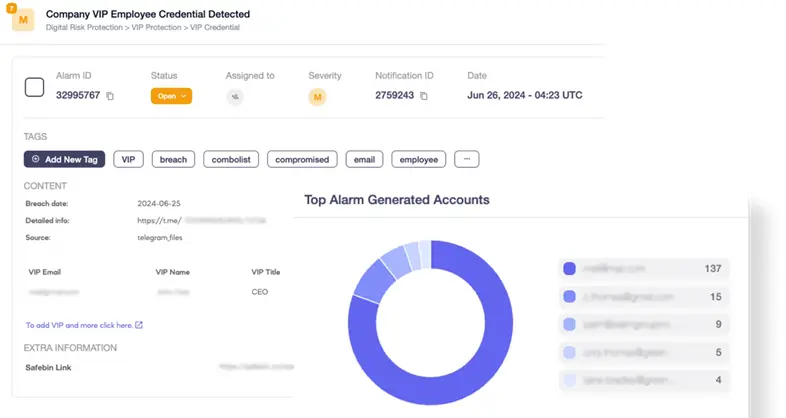
- Employee Data Breach
- Stealer Malware Tracking
- Hacker Discussions Monitoring
- Dark Web Search Engine
- Telegram & Discord Channel Monitoring
- Ransomware Activity Monitoring
- VIP Monitoring
- Buyback Blackmarket leads
Brand Protection
- Brand Abuse Protection
- Data Leak Prevention
- Typosquatted Domain Risks
- Social Media Risks
- Credit Card Fraud Risks
- Rouge Mobile Apps
- Integrated Takedown
Attack Surface Management
- Digital Asset Monitoring
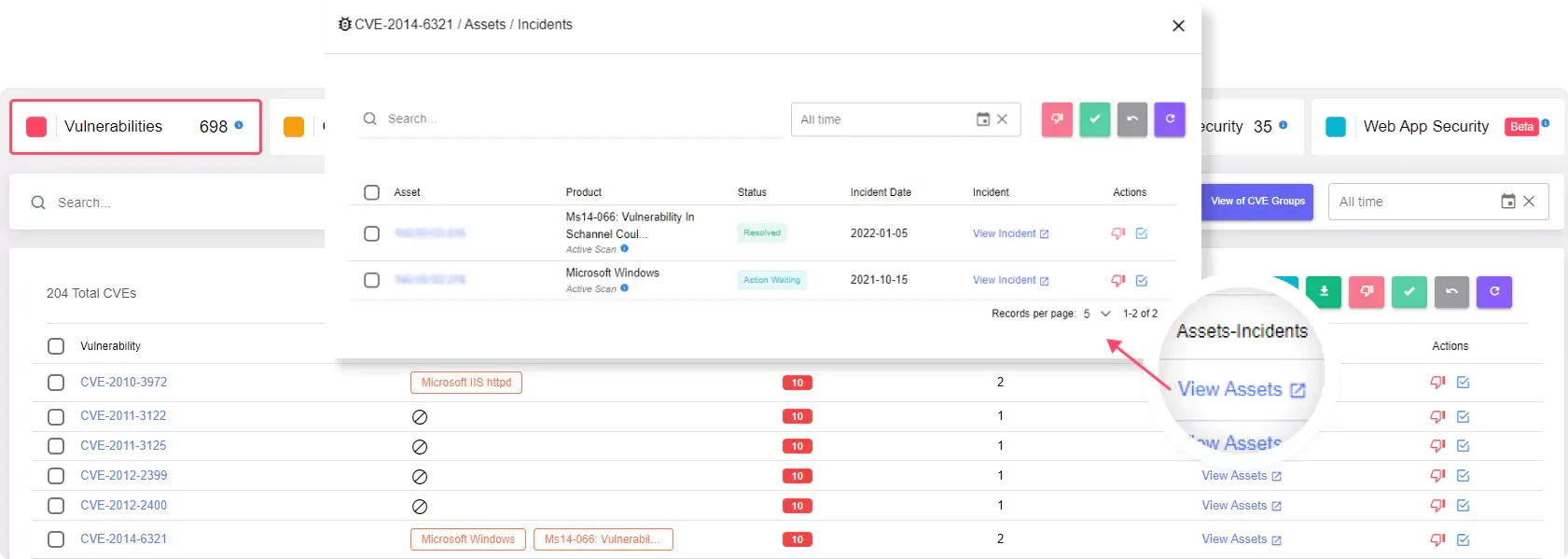
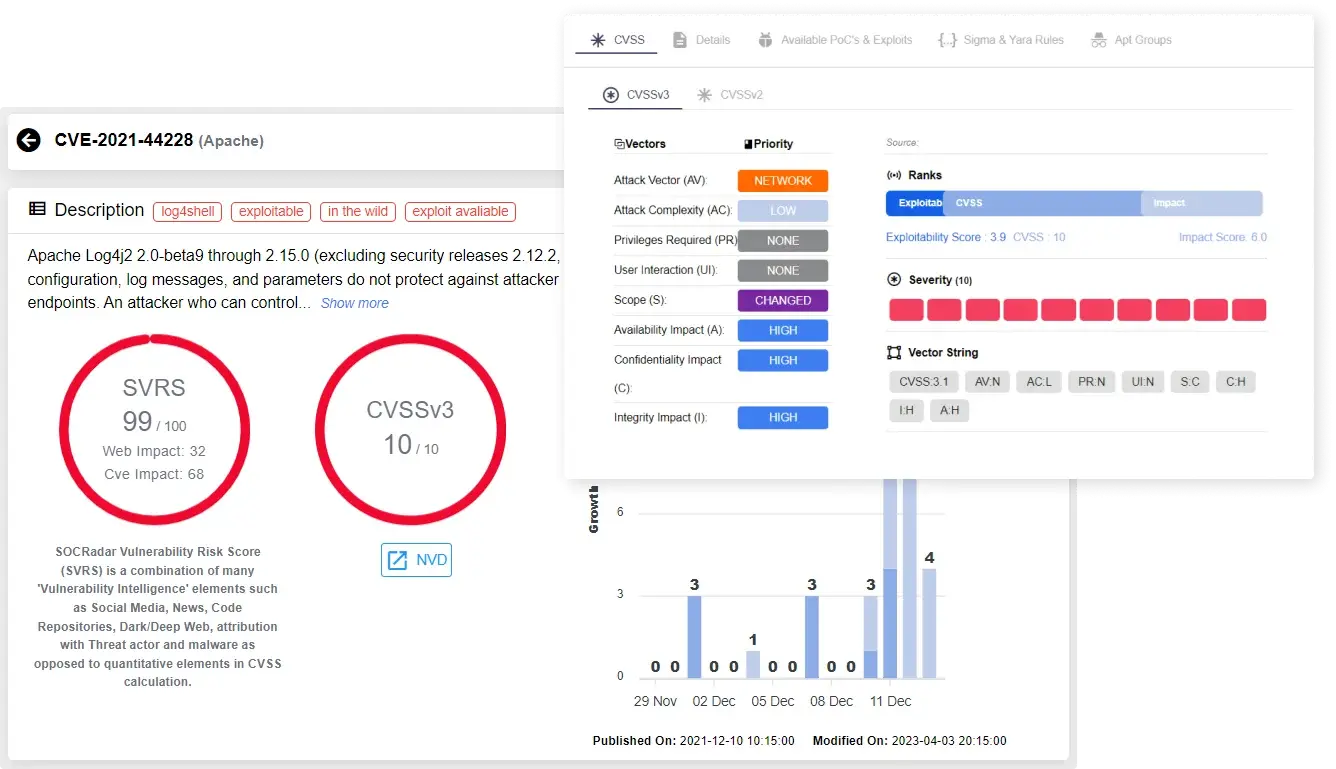
- Critical Vulnerability Alerts
- Shadow IT Detection
- Identify Digital Blind Spots
- Digital Identity Monitoring
- Actionable Insights
- Advanced DNS Monitoring
Starting at:
$ 8,999.00 / year
Digital Risk Protection
Start NowDark Web Monitoring
- Covers 1 domain
- Blackmarket Monitoring
- Employee Data Breach
- Stealer Malware Tracking
- Hacker Discussions Monitoring
- Dark Web Search Engine
- Telegram & Discord Channel Monitoring
- Ransomware Activity Monitoring
- VIP Monitoring
- Buyback Blackmarket leads
Brand Protection
- Brand Abuse Protection
- Data Leak Prevention
- Typosquatted Domain Risks
- Social Media Risks
- Credit Card Fraud Risks
- Rouge Mobile Apps
- Integrated Takedown
Attack Surface Management
- Digital Asset Monitoring
- Critical Vulnerability Alerts
- Shadow IT Detection
- Identify Digital Blind Spots
- Digital Identity Monitoring
- Actionable Insights
- Advanced DNS Monitoring
Starting at:
$ 15,999.00 / year
External Attack Surface Management
Start NowDark Web Monitoring
- Covers 1 domain
- Blackmarket Monitoring
- Employee Data Breach
- Stealer Malware Tracking
- Hacker Discussions Monitoring
- Dark Web Search Engine
- Telegram & Discord Channel Monitoring
- Ransomware Activity Monitoring
- VIP Monitoring
- Buyback Blackmarket leads
Brand Protection
- Brand Abuse Protection
- Data Leak Prevention
- Typosquatted Domain Risks
- Social Media Risks
- Credit Card Fraud Risks
- Rouge Mobile Apps
- Integrated Takedown
Attack Surface Management
- Digital Asset Monitoring
- Critical Vulnerability Alerts
- Shadow IT Detection
- Identify Digital Blind Spots
- Digital Identity Monitoring
- Actionable Insights
- Advanced DNS Monitoring
Need Something More Customized?
Our security experts can help you find the best solution for your organization.
No matter your size or industry, we have a solution for your needs
Frequently asked questions
Here are some common questions about
Cyber Threat Intelligence.
According to Gartner, “threat intelligence is evidence-based knowledge, including context, mechanism, indicators, implications, and actionable advice, about an existing or emerging menace or hazard to assets that can be used to inform decisions regarding the subject’s response to that menace or hazard”.
EC Council’s definition is very similar, “threat intelligence is the analysis of data using tools and techniques to generate meaningful information about existing or emerging threats targeting the organization that helps mitigate risks”.
In simple terms, CTI helps you understand who might attack you, how they might do it, and how you can stop them.
Cyber Threat Intelligence turns raw threat data into actionable insights — helping organizations stay ahead of attackers and build smarter, more adaptive defenses.
Cyber threat intelligence aims to help institutions and organizations understand the risks of cyber attacks or cyber threats. These attacks can range from zero-day attacks, crypto viruses, APTs (Advanced Persistent Threats), botnets, or exploits. These threats are reported with the intelligence activities after being reviewed by CTI analysts to provide special protection methods to assist in an active defense in your organization.
In today’s evolving cyber landscape, defending without intelligence is like flying blind.
Cyber Threat Intelligence (CTI) gives organizations the insights they need to anticipate, detect, and respond to threats faster and smarter.
To develop a defense strategy against attackers, organizations need to know how hackers operate, how they function, and what techniques they use.
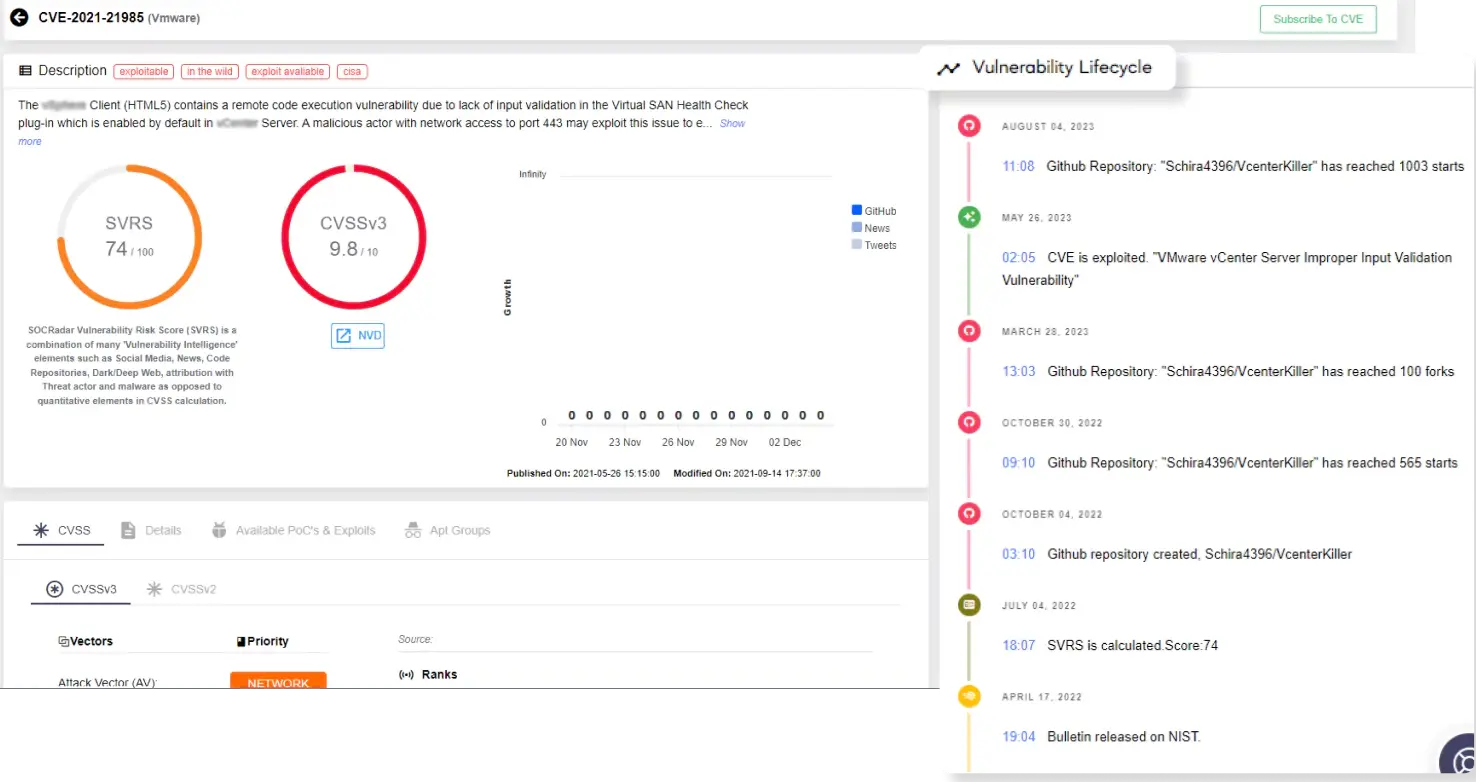
Cyber-threat intelligence allows companies to identify the dynamics and consequences of risks, improve security plans and structures, and reduce their attack potential to minimize damage and defend their network.
- Focus on actionable alarms: the legacy threat intelligence solution provided only feeds and (Indicator of Compromise) IOCs, which were not actionable. But organizations started to need more and more of the latest intelligence about them. With real-time intelligence on threat actors, botnets, malware, and data from the dark web and the deep internet, organizations need to detect phishing domains targeting their customers.
- Collect, Verify, and Prioritize External Threats: CTI can deliver the hard work for your business with enriched intelligence that allows you to apply smarter defense and improvement processes.
- Detect Forgotten Assets and Monitor Attack Surface in Real-time: CTI can determine the blind spots by following the changing attack surface all the time.
- Prevent Data Loss: by using CTI, cyber threats can be detected, and security breaches can be prevented from disclosing confidential information.
- Strategic Cyber Threat Intelligence: It utilizes comprehensive pattern and emerging risk analysis to provide an outline of future cyber-attack implications.
- Operational Cyber Threat Intelligence: It is mainly used to make resource management decisions regarding actual and potential risks, historical resources, affiliations, and motives of threat actors.
- Tactical Cyber Threat Intelligence: Primarily, its main target is a technically trained audience and allows them to learn more specific details on threat actors’ tactics, techniques, and procedures (TTPs).
- Technical Cyber Threat Intelligence: It focuses on the technological details suggesting a cyber-security threat, such as phishing email lines or malicious URLs.
| Information | Intelligence |
| Unfiltered and raw data | Processed and sorted data |
| Not evaluated | Evaluated by Threat Intelligence Analysts |
| Too much-aggregated data | Only useful data |
| Not actionable | Actionable |
| Disconnected, incomplete, irrelevant | Connected, completed, and relevant |
Information:
- Raw, unprocessed data or facts — observations without context or analysis.
- Information alone doesn’t tell you what’s relevant or what to do next. It’s just raw input.
- Simple Analogy: Raw ingredients (flour, eggs, sugar)
Intelligence:
- Information that has been analyzed, contextualized, and evaluated to produce actionable insights.
- Intelligence helps you make decisions. It’s processed information + context + relevance.
- Simple Analogy: Finished cake, ready to serve and use.
Frequently asked questions
Here are some common questions about
Dark Web.
The Dark Web refers to a part of the internet deliberately hidden and inaccessible through standard web browsers. Due to its encrypted nature, it is often associated with anonymous and illicit activities. While the Dark Web serves legitimate purposes, such as protecting users’ privacy, it can also host illegal marketplaces, forums, and communication channels for cybercriminals.
For businesses, the dark web is where stolen credentials, leaked data, malware, and hacking services are traded or shared, often months before breaches become public.
Advanced Dark Web monitoring works by continuously scanning hidden corners of the internet that aren’t indexed by traditional search engines. The monitoring service gathers information from various sources. The collected data is then analyzed to identify mentions of your organization, ultimately alerting you of any concerning findings.
PurpleSentry Advanced Dark Web Monitoring empowers individuals and organizations to safeguard their data and reputation proactively. Our advanced tools continuously scan hidden corners of the internet, including forums, marketplaces, and chat rooms. Using cutting-edge techniques, we identify mentions of your organization, potential data breaches, or cyber threats, even if your name isn’t explicitly mentioned. Receive timely alerts with details about the source and potential risk, allowing you to take action and mitigate threats before they escalate.
Dark Web Monitoring helps organizations proactively detect cyber threats. To minimize risks such as identity theft, financial fraud, and data breaches, continuous monitoring of dark web activity is essential.
Without dark web monitoring, businesses are blind to early warning signs that they are exposed or targeted.
Dark Web Monitoring is crucial for businesses of all sizes, from enterprises to small businesses, as well as individuals, government agencies, and financial institutions.
If your business has users, customers, employees, or sensitive data online, Dark Web Monitoring is no longer optional — it’s a critical part of modern cybersecurity defense.
Dark Web Monitoring can help detect early warning signs associated with ransomware attacks, but it doesn’t directly detect ransomware infections on your network.
Ransomware groups often operate on dark web forums, where they share stolen data or discuss upcoming attacks. Advanced Dark Web Monitoring helps identify these threats early, providing organizations with crucial insights to mitigate ransomware risks before they escalate.
Frequently asked questions
Here are some common questions about
Brand Protection.
Brand Protection is a cybersecurity strategy that focuses on identifying, monitoring, and mitigating digital risks that can impact an organization’s information security and business operations. These risks can include data breaches, phishing threats, brand impersonation, data leakage, exposed credentials, cyber fraud, and many more.
BP involves the use of various tools and technologies to constantly scan the digital landscape — the web, social media platforms, deep and dark web, mobile apps, and other digital channels — for potential risks to an organization’s digital assets.
As businesses continue to expand their digital footprint, they expose themselves to increased risk. BP helps businesses proactively identify and manage these risks, protect their reputation, maintain customer trust, and avoid potential regulatory fines.
In today’s digital world, your brand isn’t just a logo — it’s your identity, reputation, and trust in the eyes of customers, partners, and investors.
Without Brand Protection, businesses are blind to external risks that can harm customers, damage reputation, and drain revenue
Brand Protection (BP) helps businesses safeguard that trust from online threats, abuse, and misuse.
- Typosquatted and fake domains
- Phishing sites and email scams
- Rogue mobile apps
- Brand impersonation on social media
- Counterfeit products in online marketplaces
- Dark web mentions and data leaks
Brand Protection (BP) platforms gather and analyze information about potential threats that could harm the organization’s digital assets. This intelligence is then used to strengthen the organization’s cybersecurity defenses.
Brand Protection doesn’t just protect your name — it equips you with real-world, outside-in intelligence to strengthen your entire cybersecurity posture.
Frequently asked questions
Here are some common questions about
External Attack Surface Management.
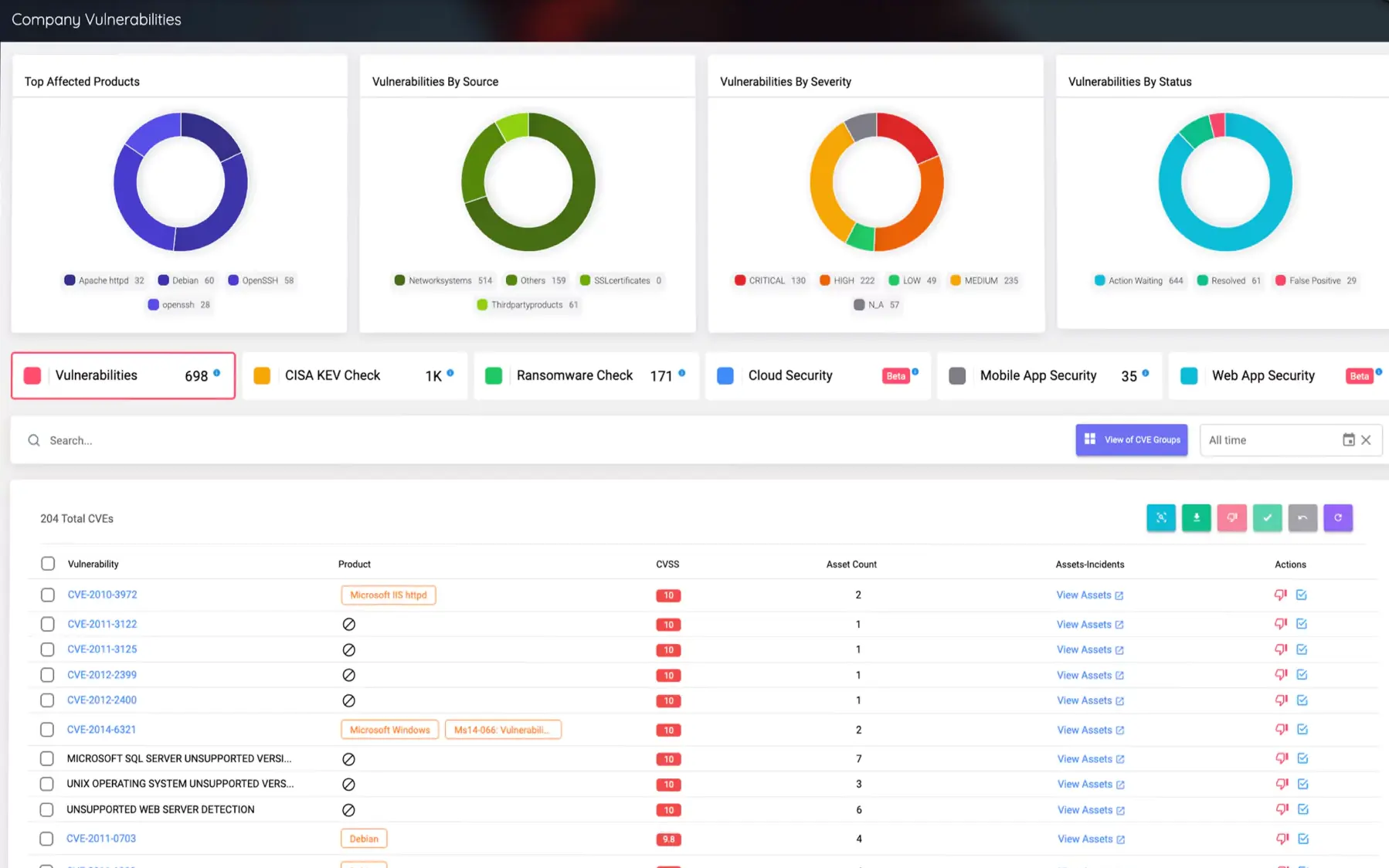
The attack surface is the point or vector through which an attacker enters the environment and is merely a list of all possible ways in which the attacker can enter a device or network and extract data. In other words, the attack interfaces can be described as a collection of different points where unauthorized users could infiltrate an IT environment. There are a number of points from which attackers could attempt to penetrate the environment, such as access to the network, access from a remote location, or access via a network connection.
Attack surface refers to any asset such as domain infrastructure, website services, cloud technologies, etc. that is open to the Internet and can be exploited by the attacker.
External Attack Surface Management (EASM) is the continuous process of discovering, monitoring, and managing all internet-facing assets an organization has — to identify exposures before attackers do.
In simple terms, it’s like putting a spotlight on everything outsiders can see about your organization online — and making sure it’s secured.
Today’s organizations are constantly expanding their digital presence — across cloud services, web apps, APIs, remote access, and third-party integrations.
But every external asset you own is a potential doorway for attackers.
EASM gives you the outside-in visibility you need to stay ahead of cyber threats.
Without EASM, you’re blind to external risks attackers can see.
With it, you gain a proactive, always-on early warning system that helps you reduce exposures, strengthen defenses, and stay ahead of cyber threats.
An organization’s external attack surface is everything connected to the internet that an attacker can see, probe, and potentially exploit. This can include websites, email servers, cloud storage and services, web applications, APIs, Internet of Things (IoT) devices, and all public-facing assets, services, and exposures — whether known or unknown — that could become entry points into your organization.
Attackers only need one weak spot to break in.
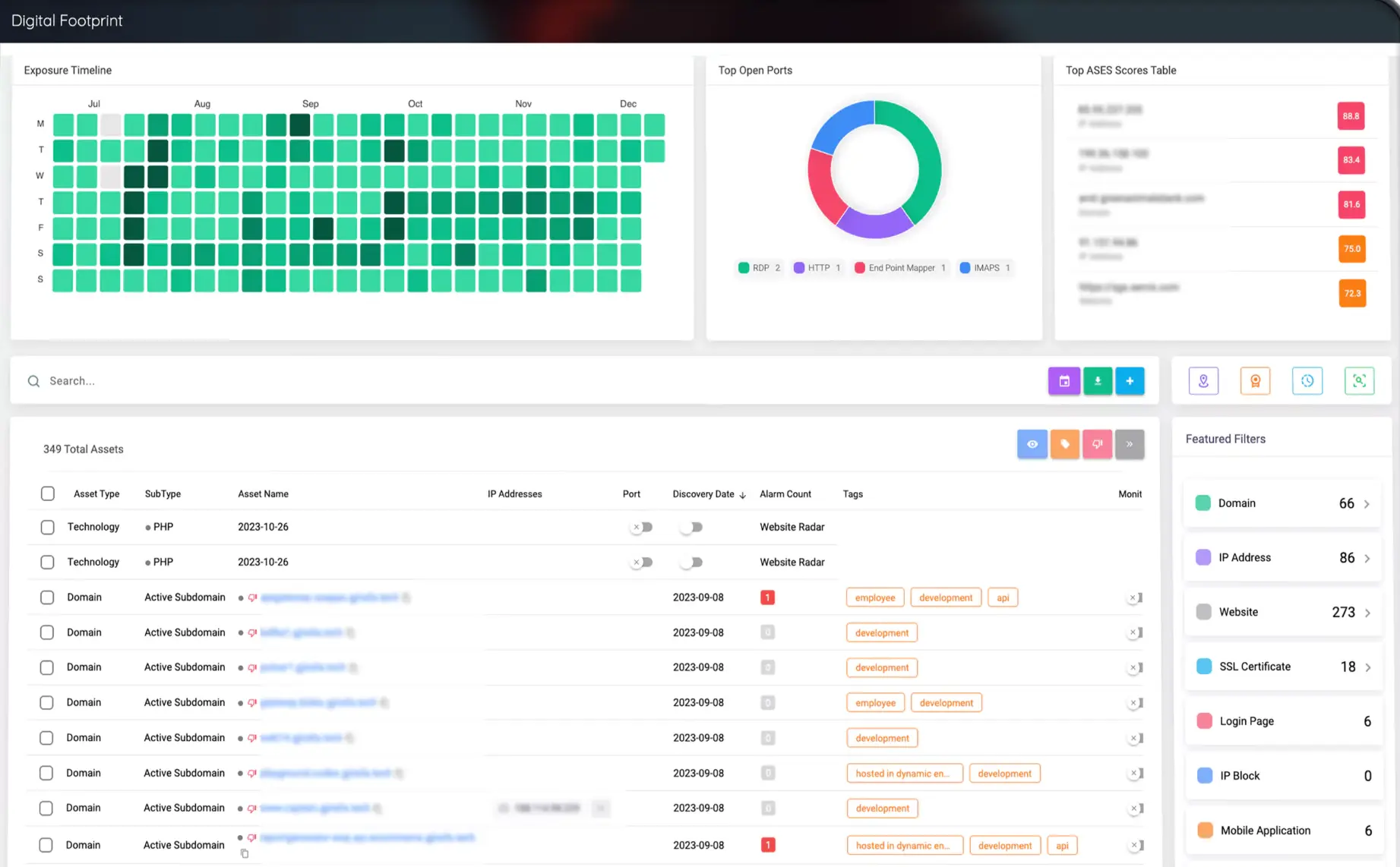
A digital footprint is the complete record of all the online assets, activities, and traces an organization leaves across the internet — both intentionally and unintentionally.
To manage the attack surface, it is necessary to first identify all assets open to the Internet. The digital footprint is important because companies have many assets that they do not know or forget, as well as assets they know and manage. For instance, some promotional pages opened for marketing purposes may have been forgotten to shut down or not notified to the security team. Any assets that are forgotten or not configured for security threats could be harmful to companies. Because attackers always prefer to attack companies over unmanaged assets.
Your digital footprint defines how you appear to the outside world — including customers, partners, and attackers. Managing it is essential to reducing risk and improving your security posture.
Organizations can reduce their external attack surface by regularly conducting vulnerability assessments and penetration testing, timely patching and updating software, employing strong access control measures, securing APIs, encrypting data, and utilizing other cybersecurity best practices.